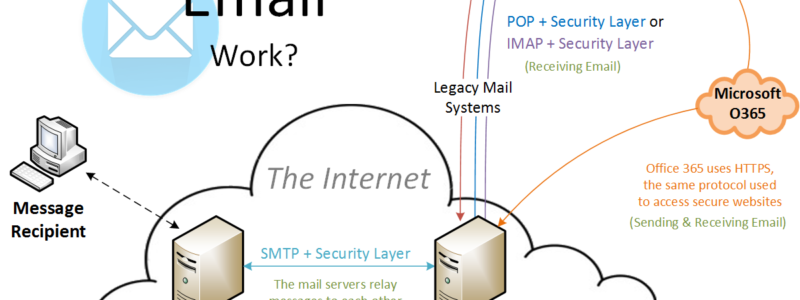
How Does Email Work?
Creating and sending an email may seem like a magical process that happens all on its own, but it’s actually a little more complicated than that. So how does it work? To get an email to your intended recipient, you send an email from your server to their server via the internet. This is done using SMTP (Simple Mail Transfer Protocol). Seems simple, right? It doesn’t stop there. In order to ensure the safety of that email’s contents, your everyday applications use TLS (Transport Layer Security) to send that email securely across the network.
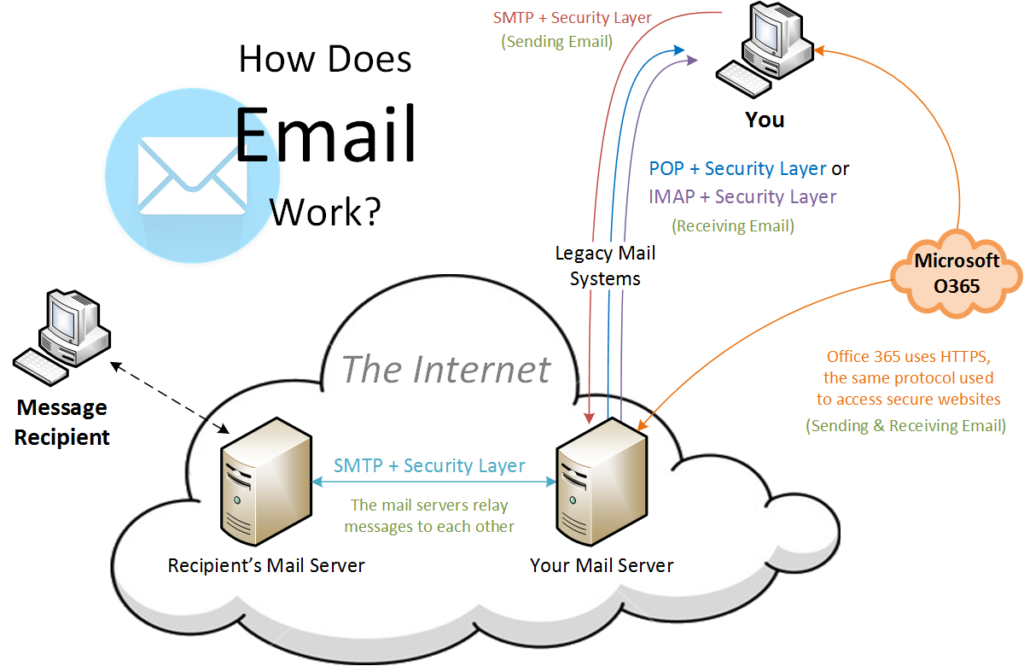
When the recipient receives the email, they can access it from their mail server using methods such as POP or IMAP. When using POP (Post Office Protocol), your email application downloads the email from your mail server to whichever device you’re using. If a full version is downloaded to that device, you can access it whether you’re connected to the internet or not. However, if something happens to that device and you didn’t update your default settings to keep a copy of that email on the mail server, then those emails could be lost. When using IMAP (Internet Message Access Protocol) you can access the email from any device that has access to the internet regardless of your location. This may seem like an easy enough decision between the two, but retrieving email from your mail server ALSO needs additional security levels! When using Microsoft Office 365, all of these security measures are built in.
Spam Filtering
When opening your email the last thing you want to see is a bunch of junk. Reading your emails should be a simple, straight forward process. A spam filter does just like the name implies; it filters what is known to be a spam email to either a spam folder, a separate inbox, or blocks the spam completely. Spam creators have become more creative in their attempts to avoid having their email rerouted. This has required spam filters to become more intelligent at catching what’s legitimate email and what is not. Spam filter methods include: third party, desktop, or built-in.
Email Encryption
Some emails are more confidential than others. An email containing social security or credit card numbers is a perfect example. Encrypting an email allows a sender to only allow a specific recipient to open an email by using a private key to access it. There are many different forms of email encryption such as Zixmail, which was mentioned in The Ping: Office 365 Add-Ons. When you send an email through Zixmail, it is delivered using a plugin installed in your email software. The email comes from your existing email address and sends a challenge response that prompts the user to log in to retrieve secure messages. By logging into the portal to review the message, a notification can be sent to the sender in order to let them know that the recipient logged in and reviewed the message. Many of our current financial institutions use this to send important documents to clients. This add-on is available not only for Office 365 but other Outlook client users as well.
Your UniVista Team
*Celebrating 20 Years of Customer Satisfaction*