*Special Alert* – Extortion Email Scam
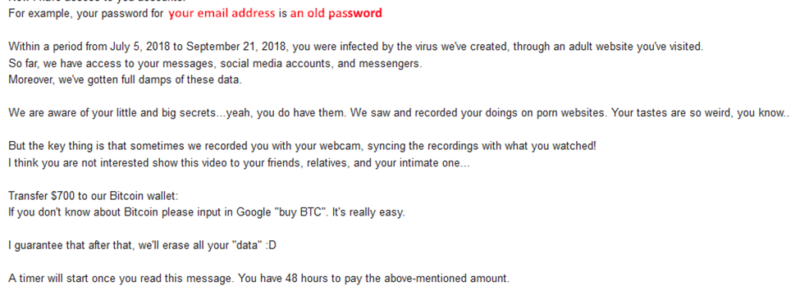
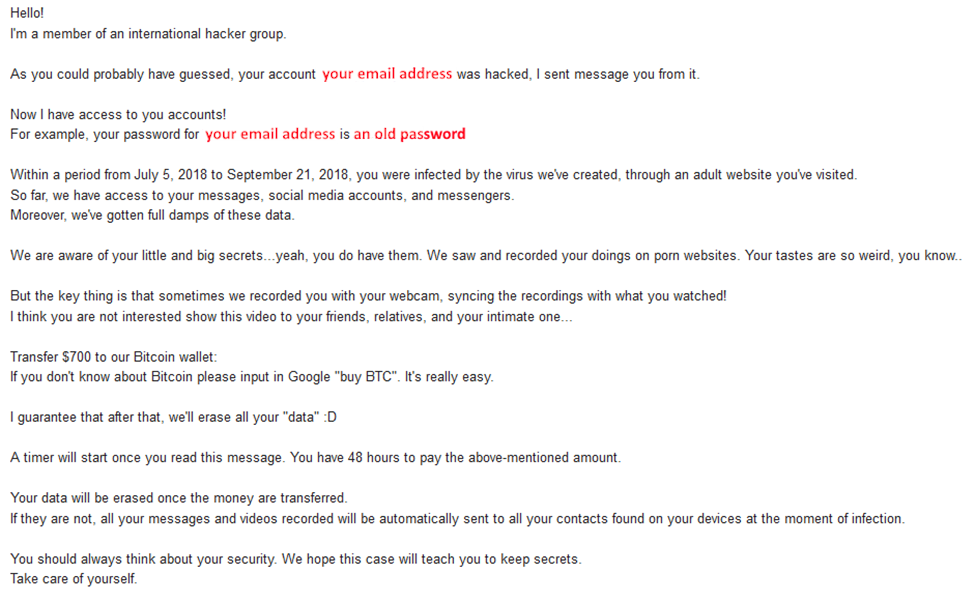
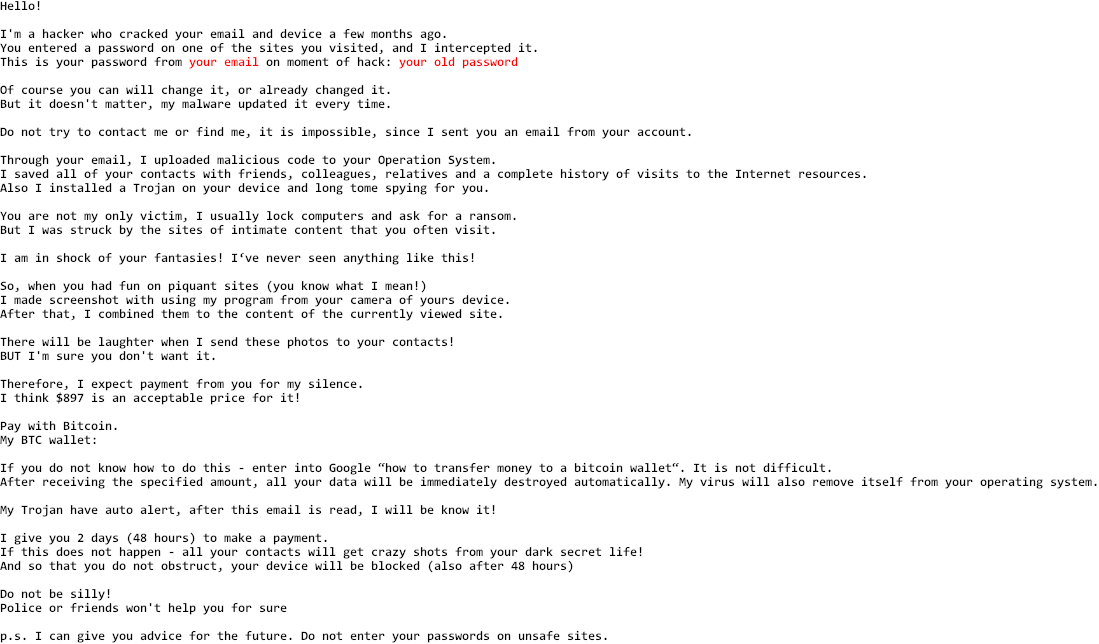
A worrying new type of phishing email is going around using stolen data from high-profile websites. These emails include a password that has been used with the user’s email address in the past in an attempt to scare that person into sending the scammer money (typically Bitcoin). Since the emails include personalized information, they appear credible in ways typical phishing emails do not. Typically, the scammer is claiming that they have recorded “compromising activity” and blackmailing the user for their silence.
Within the last year, Facebook, MyHeritage, Ticketfly, Under Armour, and several other high-profile services have been compromised.
How does this happen?
- A website is compromised (“hacked” or “breached”) due to poor security.
- That website’s user database (including emails and sometimes passwords) is stolen (“leaked”).
- This stolen information is generally made available on the web.
- Scammers obtain one of these lists of emails and passwords.
- Scammers send messages to your email and include the password from the list.
- You open the email and are worried that you have been infected.
Example emails
What should I do if I receive one of these emails?
First, don’t panic. Under no circumstances should money be sent to the specified address. Don’t respond to the email or open any attachments. Change your email account password and account recovery options immediately! If you know that password is in use anywhere, change it immediately! There is a free tool available at this website that can list known breaches that an email address was a part of. However, this is not a definitive list, there are breaches that fly under the radar.
Now what? You’ve heard it before and probably have hesitated or delayed changing your passwords or account security settings because it seems like a daunting task. Well, it’s time. Especially if you’ve seen an email like this in your inbox. Grab a cup of coffee or tea, kick your feet up and spend an hour making the changes…
What changes should I make to be more secure?
Most importantly, do not re-use the same password for multiple different logins! This is the only sure way to prevent one site’s hack from compromising your whole online identity. Beyond that, there are actually quite a few ways to better secure your accounts:
- Passwords – Here are the recommended rules of creating a new password to consider…
- Do not use any names (e.g., your first name, your middle name, your last name, your logon name, spouse’s name, children’s name, etc.).
- Do not use common information (e.g., license plate number, address, driver’s license number, social security number, telephone number, brand of automobile, etc.).
- Do not use a single, common word (words found in a dictionary).
- Do not use repeating characters or single digits.
- Make your password easy to remember.
- Consider using a “passphrase” as a password, such as “UniVistaislookingoutforme!”
- Use a minimum of 7 characters for your passwords.
- Use both upper- and lower-case letters (e.g., A,a,B,b, etc.).
- Use non-alphanumeric characters (e.g., 1, 2, 3, !, @, etc.).
- Two-factor authentication – You may have been presented with the option to enable this on your banking website, or your Gmail account, etc.… Again, now is the time to go ahead and set this up. You may have the option of simply adding a text confirmation as a second authenticator.
- Account Recovery Settings – Check your security settings, what happens if you get locked out? Imagine this… someone gains access to your email address and password from one of any of these breaches. If you use that same password everywhere, they now have access to your Facebook, your email and can completely hijack your email account by changing your account recovery options. This really does happen.
- Login Name – If you have an option to use a different login name than your email address, enable it. You may have noticed online banking has moved to requiring some or all of the above as well as a login name different from your email address. That’s because it’s all too common and that information is readily available and easy to obtain, so half the job to access your info is done.
Follow up and prevention…
How is your computer? Did you click on the email, do you think it’s infected or compromised? Do you want to make sure your co-workers and/or employees are aware of these security risks and recommended actions? Let us know. We can help. We can scan your computer and setup training. Contact your UniVista Account Manger today!
Reference Websites and additional information available at the following sites:
FBI Advisory for this type of scam
https://www.ic3.gov/media/2018/180807.aspx
Secure tool to check if your email address is included in various breaches