
![]()
Downloading or receiving emails from unknown sources is a risk that we all know can have dire consequences, but that seemingly innocent Word document is now more of a security risk than ever before.
It was recently discovered that hackers are starting to take advantage of a unique security flaw to gain access to your computer. Previously they would do this by sending you Word documents that contain what are known as “macros.” When enabled, malicious macros can download viruses directly to your machine. Since Microsoft began issuing security warnings for macros, hackers have now found ways to abuse DDE, or Dynamic Data Exchange. DDE is a process that Microsoft uses to share data between applications. For example, Mail Merge can take data from an Excel document and insert it into a Word document. However, it also turns out that hackers can use DDE to send silent download commands in the background of your computer.
What we’ve known about the traditional document risk (macros):
- Macros are instructions for automation that can do useful things like auto-formatting, running calculations, and reading information from other data sources.
- Most documents that you receive do not include macros, so they are typically not allowed to run by default.
- Unfortunately, hackers can use these macros download viruses from the Internet and then use Microsoft Word as a jumping-off point into gaining access into your computer.
How do we protect ourselves?
- In recent versions of Office, macros are disabled by default and you need to acknowledge that you trust the publisher of the document before enabling them.
- Never consent to this trust unless you’re positive you know the document and its macros are legitimate.
- Always stop and think twice before indicating that you trust a document’s publisher.
- Even if a message is from somebody you communicate with regularly, would a document claiming to be an invoice really need permission to run scripts on your computer?
What’s new this time?
- DDE, or Dynamic Data Exchange, is a protocol for sharing data between the Office applications that is enabled by default and does not have the same security warnings.
- This is a core functionality of Microsoft Office and cannot easily be disabled without affecting a good portion of the application functionality.
- Hackers are able to use this method to infect your computer outside of Microsoft Word by having the document use DDE to send a command to Windows PowerShell that will download and install the virus without your knowledge.
How do we protect ourselves?
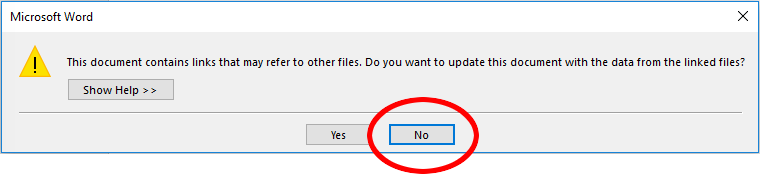
- When these documents are first run on a new computer, we will be prompted before any external data is allowed to be linked, so we have the opportunity to say NO.
- Even though Microsoft isn’t warning us about potential security risks and the need to be wary of the document’s origins, the same precautions as with traditional Macro attacks should be followed.
- Always be cautious of external documents and messages that are asking your permission to do something on your computer.
On a lighter note:
Did you know that you can find the Millennium Falcon of Star Wars fame on Google Maps? Just type 51°23’01.4″N 0°34’54.8″W into Google maps. Maybe Chewy is there too…
Sincerely,
Your UniVista Team
*Celebrating 20 Years of Customer Satisfaction*
